Automating the Oracle JDK installation on RHEL derivatives (such as CentOS, Oracle Linux) and Debian derivatives (such as Mint, Ubuntu) differs. This is due to different package managers and repositories. In this blog I'll provide quick instructions on how to automate the installation of Oracle JDK 8 and 10 on different Linux distributions. I chose JDK 8 and 10 since they are currently the only Oracle JDK versions which receive public updates (see here).
Articles containing tips, tricks and nice to knows related to IT stuff I find interesting. Also serves as online memory.
Friday, July 27, 2018
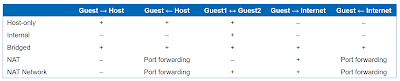
VirtualBox networking explained
VirtualBox networking is extremely flexible. With this flexibility comes the challenge of making the correct choices. In this blog, the different options are explained and some example cases are elaborated. Access between guests, host and other members of the network is explained and the required configuration is shown. This information is also available in the following presentation here.
Labels:
bridge,
bridged,
guest,
host,
host only,
nat,
nat network,
network,
networking,
virtualbox
Friday, July 13, 2018
Securely access remote content using a proxy server accessed with SSH
There are numerous occasions that I was limited in my work because of connectivity which could not be trusted. For example;
In short what you do is
- I could not download large installers due to a proxy anti virus tool which manipulated downloads causing files to become corrupted.
- I needed to visit a website to find a solution to a problem, but the local proxy server found the content offensive and disallowed me to visit the site.
- I have stayed in hotels in which I was not sure that my internet traffic was not being monitored. I was hesitant to access remote services which required credentials.
- At the airport, the public Wifi can sometimes not be trusted. Someone could run a local hotspot with the same name and become a man in the middle intercepting credentials of people connecting to it.
The method described in this blog allows you to access external resources with few limitations in a relatively secure way. It makes it easy to circumvent most content scanning/manipulation. Do mind that this method might be a violation of certain rules/regulations/policies. When in doubt, first confirm you're allowed to use it.
In short what you do is
- Run an SSH server on a different location on port 443
- On the same server which runs an SSH server, run your own HTTP/HTTPS proxy server (or use the SSH server itself as SOCKS proxy)
- Connect to the SSH server
- Map the proxy port to your local machine
- Use the configured port as proxy server in your browser configuration.
Labels:
circumvent,
company proxy,
proxy,
secure,
socks,
squid,
ssh,
tunnel,
tunnelier,
vpn
Subscribe to:
Comments (Atom)