SonarCloud is a hosted SonarQube SaaS solution which does not allow 3rd party plugins to be installed. This puts some limitations on the kind of data you can put in SonarCloud. For Java this is limited to Checkstyle, PMD and SpotBugs results. OWASP provides a Dependency-Check plugin to identify vulnerable dependencies in for example your pom.xml file. In this blog post I'll show how to get OWASP Depedency-Check data in SonarCloud without using a 3rd party plugin! Disclaimer: this solution has been created in very little time (~2 hours) and has not been seriously tested, optimized or used in production environments. Use at your own risk!
Method used
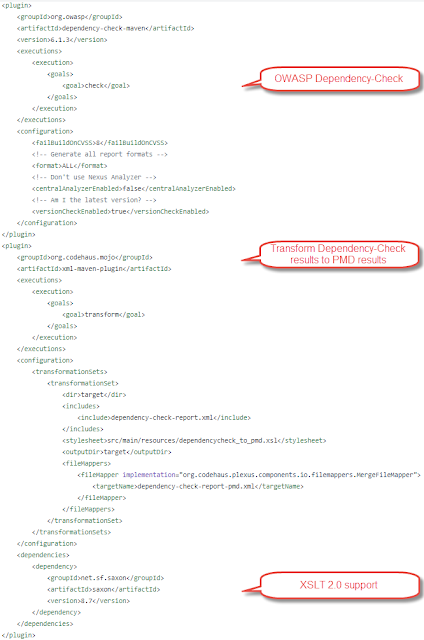
SonarCloud can import CheckStyle, PMD, SpotBugs result data. The output XML files which are generated by those plugins, conform to a specific format specified in XSDs.
The Dependency-Check results also have an XSD (
here).
I checked out the different XSDs and decided the PMD XSD was easiest to use. I created an XSLT transformation to transform the Dependency-Check result to a PMD result file and send that to SonarCloud.
Build process
In my pom.xml first the Dependency-Check report needed to be generated before I could perform a transformation. When performing the transformation, I needed to have XSLT 2.0 support to easily get the current date/time for a timestamp. This required an additional dependency. You can take a look at my pom.xml file
here. I executed a "mvn -B verify org.sonarsource.scanner.maven:sonar-maven-plugin:sonar -Dsonar.java.pmd.reportPaths=target/pmd.xml,target/dependency-check-report-pmd.xml" to generate the report and send it to SonarCloud. Notice you can specify a comma separated list of PMD files to send. Checkout my
GitHub workflow for more details on the exact build process and if you're interested,
this blog post on how I setup GitHub Actions and SonarCloud interaction.
Transformation
I created the following transformation (which you can download
here):
The challenges here were:
- the current-dateTime function which required XSLT 2.0
- transforming the CVSS3 rating to a PMD severity rating. PMD uses 1 for highest severity and 5 for lowest. CVSS3 uses 10 for highest and 0 for lowest.
- the file the issue refers to is required to exist in your code. Supplying the JAR file which causes the issue did not work so I set it to my pom.xml
- required fields like line number. 0 is not allowed so I set them to 1
- I did not find the externalInfoUrl in SonarCloud in a location I could click on it. Now you have to go to the NVD site yourself and look for the issue.
Result
The result of feeding the resulting PMD results file to SonarCloud was that I could see the issues with correct severity on SonarCloud with their description and CVE code.
This does look a bit worse though than using a 'native' Dependency-Check report and 3rd party plugin in SonarQube. For example, tags are missing and they are reported as "Code Smell" instead of "Vulnerability". Also more vulnerabilities are reported when using this method compared to the SonarQube setup. I have not looked into this in more detail but since they refer to the same file, fixing that will probably get rid of all issues.




No comments:
Post a Comment